Azure AD Connect - Javascript errors with Google SSO

So a while ago, I followed a guide to enable using Google as the login provider for all our MS365/Azure/Entra/Whatever accounts. This was a pain in the ass, as for some reason using MS to authenticate with Google is like 3 steps, but doing so the other way around is poorly documented and quite a process. (I did get it done though, and I will share that process soon.) This has worked beautifully, and since Staff have 2FA enforced for their Google accounts, in theory O365 is now protected as well.
The issues started to arise when I ran the Azure AD Connect application on the DCs.
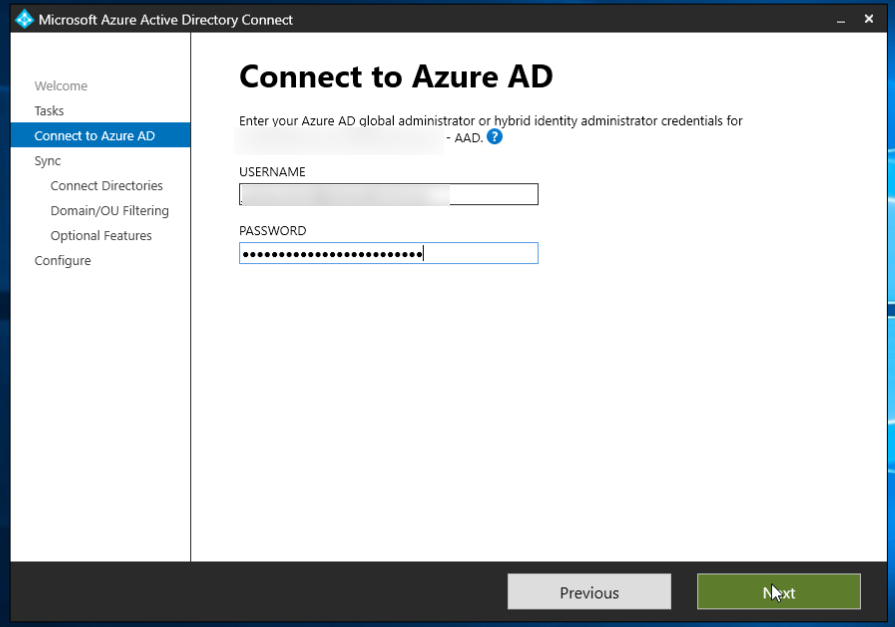
Running the application as usual, and trying to Customize synchronization options, we get the above screen. This is not a Google Login screen, and there is about a zero percent chance of this working.
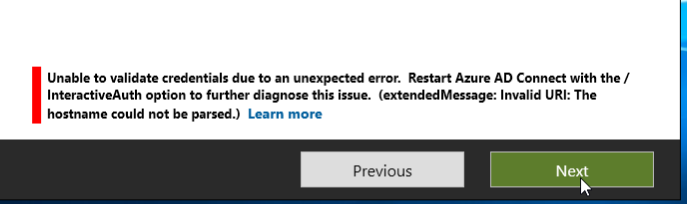
Yep, that failed. But there is hope!!
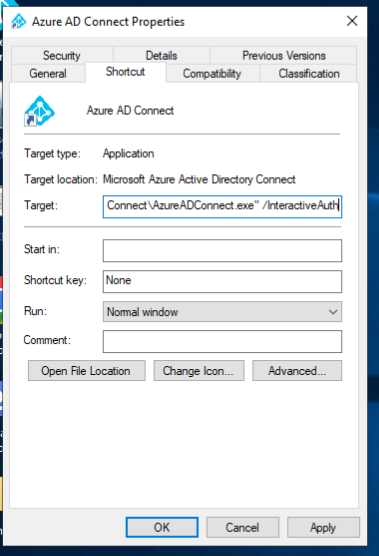
Editing the Application shortcut, or just running the exe via CLI with the argument /InteractiveAuth forces the application to bring up a browser for login instead of just logging in within the app.
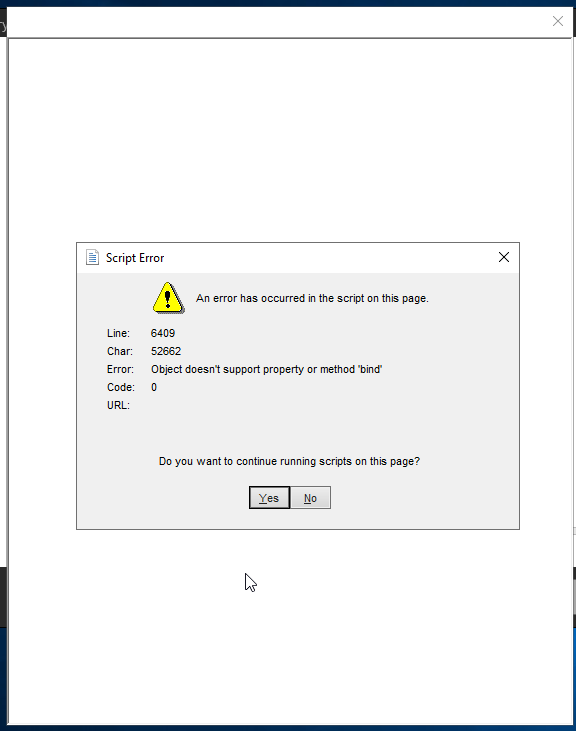
Progress, as now we at least have a browser window, but still no dice..
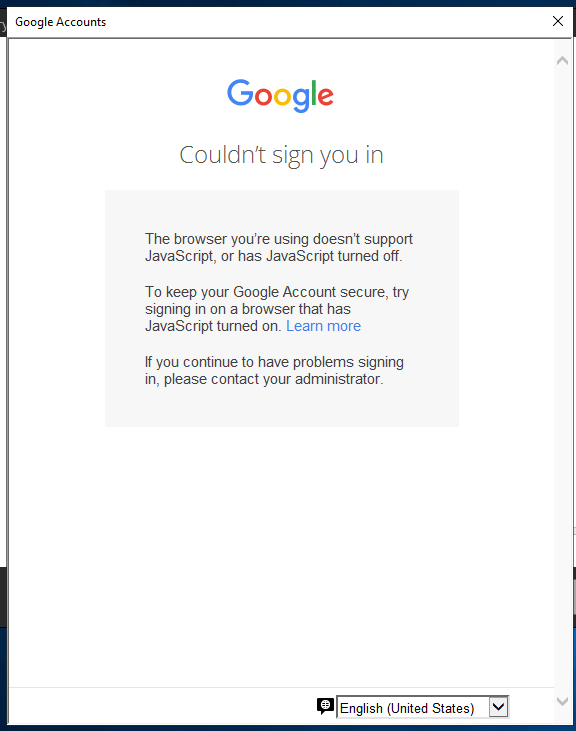
Clicking Yes on all the prompts also doesn't work.
From here I fiddled with Internet Explorer's trusted sites, adding Microsoft and Google sites to the list. It did absolutely nothing.
What's next?
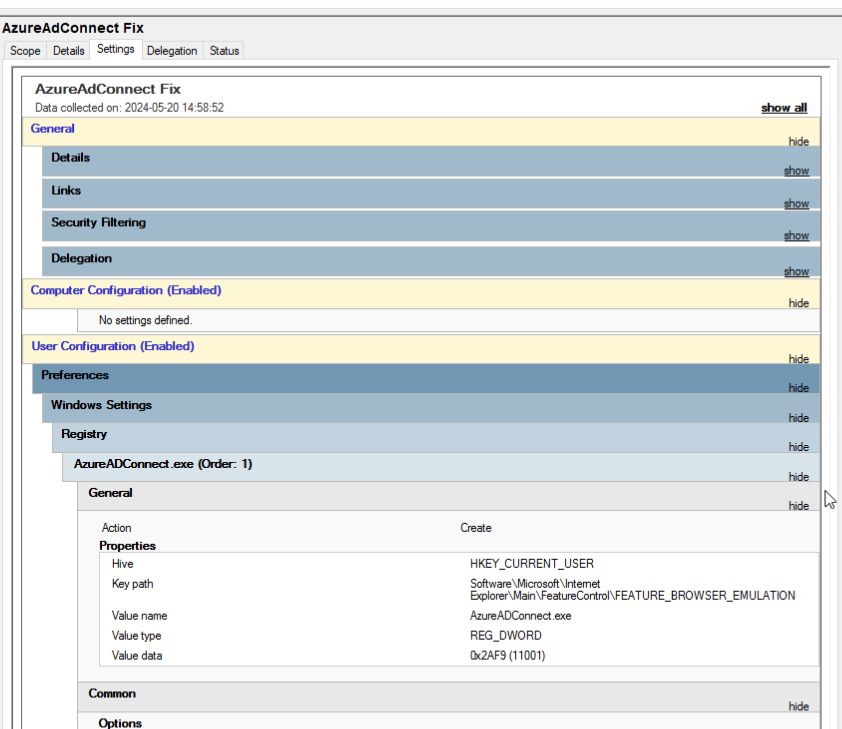
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BROWSER_EMULATION\AzureAdConnect.exe = dword:0x00002af9
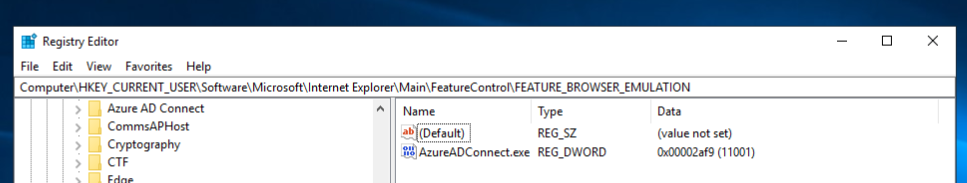
I found a post on the Microsoft Forums about a similar error in Outlook.
The solution was a registry entry. I modified that entry to AzureAdConnect.exe instead of Outlook.exe. Next, I logged out and back in.
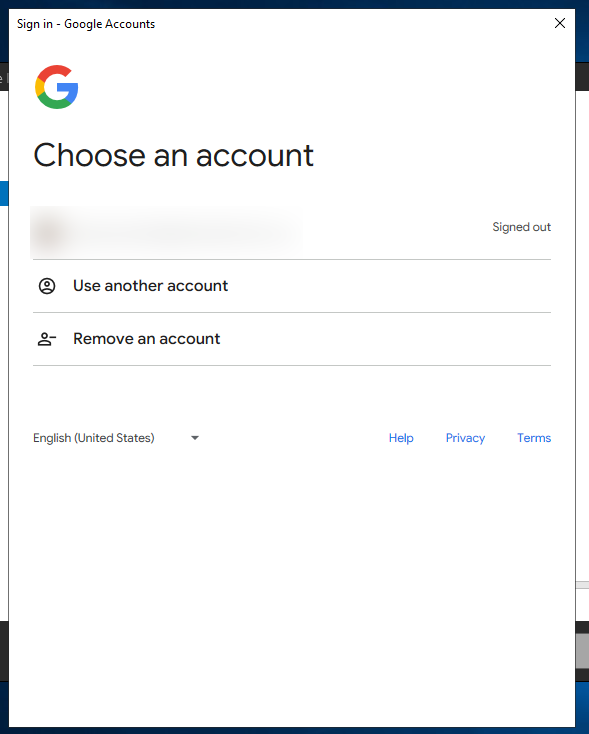
Success!!!! Why does this work? Well, Azure AD Connect, much like many garbage MS apps, uses an embedded Internet Explorer browser (yes, even if Internet Explorer is not installed) to render the login page. Changing the mode for this application enables at least Javascript, which allows it to work.
There is some more information over on Malwarebytes about this feature.
Finally we slap that Registry entry into a GPO, and apply it to whatever users log in to your Domain Controllers: