Encrypting a Drive or Partition in Linux with LUKS

Say we have a system where we need a single encrypted drive for all our rare and expensive Linux ISOs. Say we don't want to enter a password to decrypt the drive every time we boot. Say in the event the drive gets stolen or tossed, we don't want to worry about it at all. What we'd use to encrypt it is LUKS. Here's how to do that, in the laziest way possible.
First, make sure cryptsetup is installed:
apt install cryptsetup
Now let's generate a keyfile, and give it the correct permissions. Feel free to change KEYFILE to whatever seems appropriate:
dd bs=512 count=4 if=/dev/random of=/KEYFILE.key
chmod 0400 /KEYFILE.key
Side Note: If you open the keyfile, the key itself is there in plain text. You can copy it and paste it elsewhere if you like, however usually text editors will add an additional newline at the bottom of a file, which will make the keyfile not work. If you do ever paste the key into another file and save it, run this command to trim that newline off:
truncate -s -1 /KEYFILE.key
This guide is sort of operating under the assumption that you have a single drive, and you want the whole thing encrypted with one big partition. Now you need to figure out which device you want to encrypt; You can list them all with lsblk or blkid commands. Go ahead and replace /dev/SD? with the correct device or partition you want to encrypt, replace CRYPT_NAME with a relevant name for the decrypted device, and replace KEYFILE.key with wherever you put your keyfile from before:
cryptsetup luksFormat --type luks2 /dev/SD? /KEYFILE.key
cryptsetup luksOpen /dev/SD? CRYPT_NAME --key-file /KEYFILE.key
Having used the luksOpen command, our decrypted device will be mounted as /dev/mapper/CRYPT_NAME
We now need to make a real filesystem on top of that, such as ext4, then mount it somewhere:
mkfs.ext4 /dev/mapper/CRYPT_NAME
mkdir /CRYPT_NAME
mount /dev/mapper/CRYPT_NAME /CRYPT_NAME
Now we need to set things up to mount automatically on boot. That means first editing /etc/crypttab and adding an entry that looks something like this:
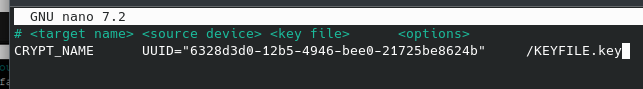
The first column is the name of the decrypted drive (where it will be mounted under /dev/mapper/), the second column is the location of the encrypted drive device, the third is the keyfile location.
I recommend using UUID to identify your disk, as the /dev/sdx thing can change after reboots. Use the blkid command to find the UUID for your drive.
Once the device is decrypted, we need to mount it just like you would any other filesystem, using /etc/fstab
Edit that file, and add an entry that looks something like this:
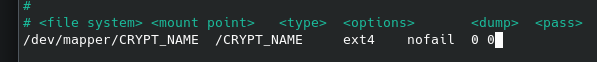
Column one is the location of our decrypted device (after /etc/crypttab happens), the second is the folder where we want it mounted, the third is the filetype, fourth is options (I recommend using nofail, as without it, if the encrypted disk can't be mounted the system will fail to boot.)




