Google Drive Permissions are a Trainwreck

More accurately, giving end users the ability to do whatever they like, and leaving Administrators with hardly any controls over what is shared and with whom, is a recipe for disaster. Last month (November 2023) it was revealed that a threat actor known as SingularityMD was exploiting misconfigured Google Groups & Drive settings to gain access to sensitive data for ransom, and they specifically targeted K-12 institutions. For a lot of us, this was a wake up call. Luckily prior to this, I had already taken the initiative of restructuring and locking down all our Google Groups, but the Drive portion of this has been an adventure...
Google provides free account licenses for educational institutions, namely the Education Fundamentals license many districts are using. Google has tools for auditing Google Drive permissions, but they are only available for those with the paid licenses ($2-$5/User). Since that isn't exactly in the budget for most of us, and doesn't really check all the boxes anyway, I've been searching for a solution.
Let's talk about what controls we do have:
Most settings can be found under Apps > Google Workspace > Drive and Docs
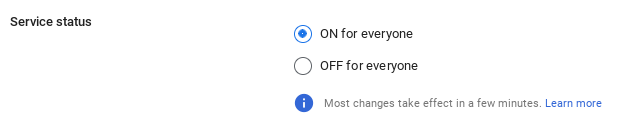
We can turn the Google Drive service on or off for everyone, a specific OU, or a specific group.
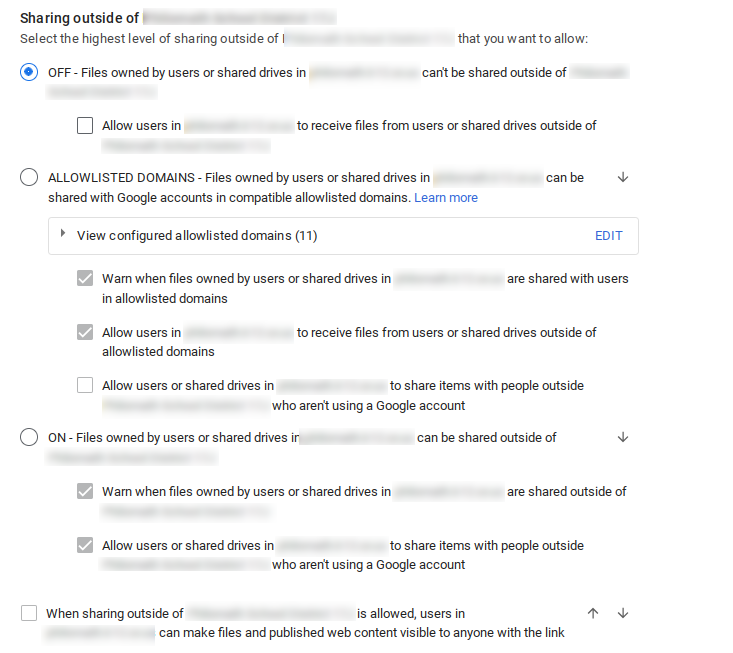
There's a lot to unpack here, but there are 3 major bodies of options:
1) Users can only share files within their organization.
2) Users can share files within their organization, and also with a select list of whitelisted domains.
3) Users can share files with anyone.
These settings apply to OUs full of users AND OUs full of Drives. I recommend keeping the two separate so you can structure policy accordingly.
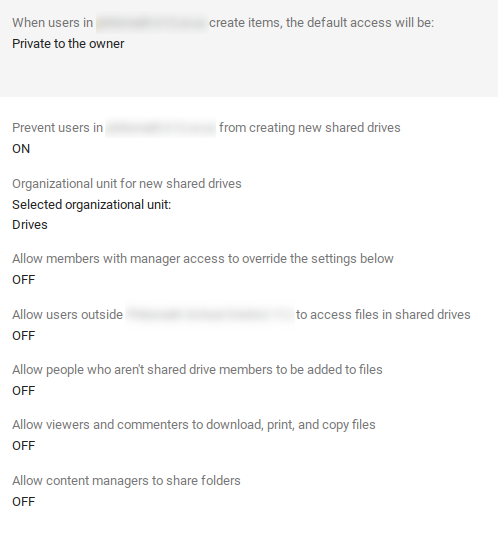
You can also set whether or not users are allowed to create Shared Drives, and what the default permissions will be for those drives. This only sets the defaults, it will not change settings for existing drives.
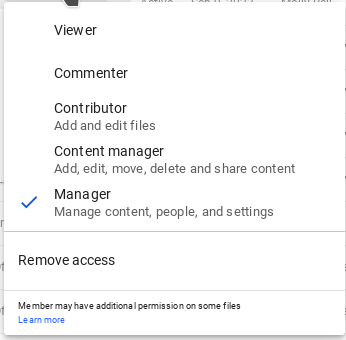
These are the roles a user can have over a specific drive.
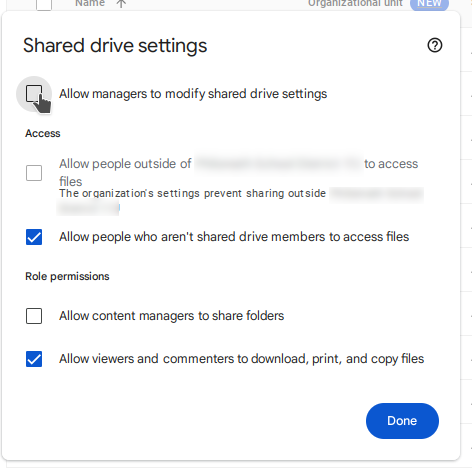
This is the settings page for a specific shared drive, mostly self explanatory.
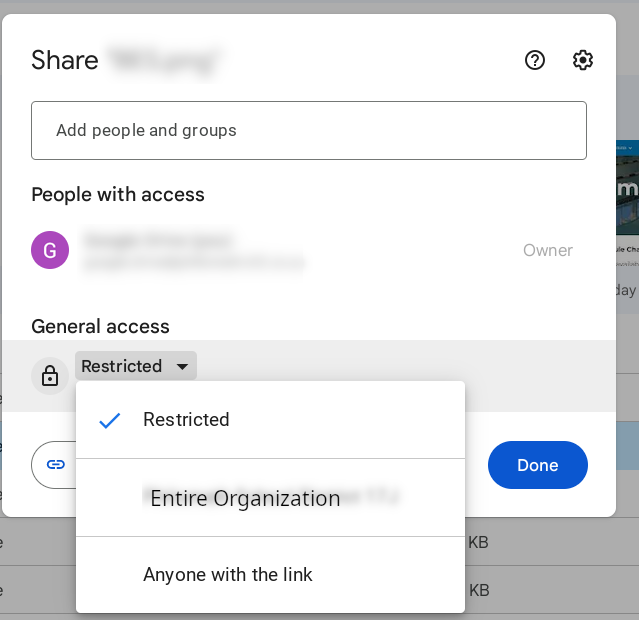
These are the options for specific files/folders.
I have four major concerns:
1) People sharing drives/folders/files with "Anyone with the link." that contain sensitive data.
2) People sharing drives/folders/files with the entire organization, (including students) that potentially contains sensitive information.
3) People sharing drives/folders/files with external accounts (so-and-so@gmail.com)
4) People sharing their drives/folders/files with their personal accounts, so they can work from home without having to log in.
Problems:
There is currently no way to stop users from sharing with the Entire Organization
and since that includes students, often students end up with access to sensitive data. More and more students are realizing this every day, but the real risk here is that most places do not change student passwords often, if ever. If a bad guy gets ahold of student passwords, now they have access to all those shared files too.
You CANNOT restrict to Only within the organization, while also allowing Anyone with the link.
The Anyone with the link option is necessary on occasion, but since the Anyone with the link setting is bundled with the setting allowing sharing outside of the Organization, places with that setting enabled will also be able to be shared with so-and-so@gmail.com!!
You CANNOT explicitly block a group or user from accessing a file.
Google Drive has no Deny option in their ACLs, so you can't, for example, add an explicit Deny All Students rule to a Drive meant for staff. You also can't work around the public links issue by blocking sharing to anyone with an @gmail.com email etc.
Suspended user's files continue to be shared.
Whatever permissions a user had on their files before their account was suspended will not go away unless the files are moved/deleted, the permissions are explicitly changed, or the account is deleted. Since there is no knowing what was being shared by those (potentially disgruntled) former employees, this is a problem. Surprisingly disabling the Google Drive service for an entire OU of suspended users has no effect. There is also no way to blanket remove all sharing permissions from a user.
You cannot modify permissions for files shared from a user's personal Drive
Even as an administrator, if the file a user is sharing is shared inappropriately, but the file is not in a shared drive, your options for remediation are seriously limited.
You cannot simply delete accounts instead of suspending them.
Every state has rules on data retention. Oregon's can be found here. There is no broad category for "Email", nor "files" but every document/communication must be classified based (for the most part) on how the content is related to the students or financial information. Some of that content is required to be retained indefinitely. Since we do not have the resources to sift through everyone's nonsense, the safe approach here is probably just to keep everything indefinitely, to the best of our ability.
Solutions
Part 1 of my solutions guide creates a pretty solid foundation for getting things sorted. More to come.




