Set up Proxmox Datacenter Manager (The Right Way)
In case you haven't heard, the team behind the world's best free & open-source hypervisor Proxmox has released something really cool... It's called Proxmox Datacenter Manager. Why is it cool? Well, previously the only way to manager multiple Proxmox servers was to put them into a cluster, but that came with some complexities. Namely, Proxmox expects that servers within a cluster are going to do things like share & sync storage, transfer VMs between eachother, etc. If one server in a cluster goes offline, Proxmox takes action to make sure the other servers aren't corrupted. These features are awesome, but if all you want to do is manage several separate non-clustered servers (or even several separate clusters) you were out of luck... until now.
Finally prayers have been answered for those of you who migrated over from VMware and have been sorely missing vCenter. This tool is only in Alpha but already it can do a LOT.
Documentation and tutorials are a bit sparse as this is brand-spanking new, so let's run through the correct way to get this set up. Go ahead and download the ISO:
Here's the link to the forum post for the initial release.
Here's the link to the downloads page
Here's a direct link to the ISO for Alpha 0.1
Now either create a VM or install it baremetal. The installation is pretty much identical to both Proxmox and Proxmox Backup Server, so I won't walk you through that part.
Head on over to https://your-server's-ip:8443
Click through the untrusted SSL certificate stuff...
...and login with the password you set during install:
Over on the left, click on Remotes:
Near the top, click the Add Proxmox VE button:
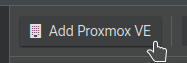
Now we need either the Server Address (IP address or the hostname/FQDN of your Proxmox server.)
This IP needs to be reachable via the web GUI from your Datacenter Manager server.
Bear in mind, if you choose to use Hostname/FQDN instead of IP and your DNS server goes down, Proxmox Datacenter Manager may lose connection. For that reason, I'd stick to using IPs unless you have a specific reason not to. We will also need the Certificate Fingerprint. We'll need to jump over to your Proxmox server for that.
Open a new tab to your Proxmox server, click on your server node and click Certificates. (If this is a cluster, just pick any of the nodes.
Double-click the pve-ssl.pem cert (or whichever cert you use for your web UI, if you've added a custom one.)
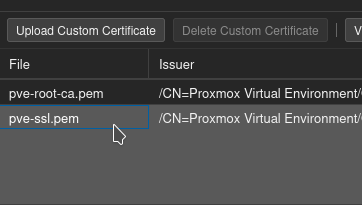
Triple click the fingerprint to select it, then copy it.
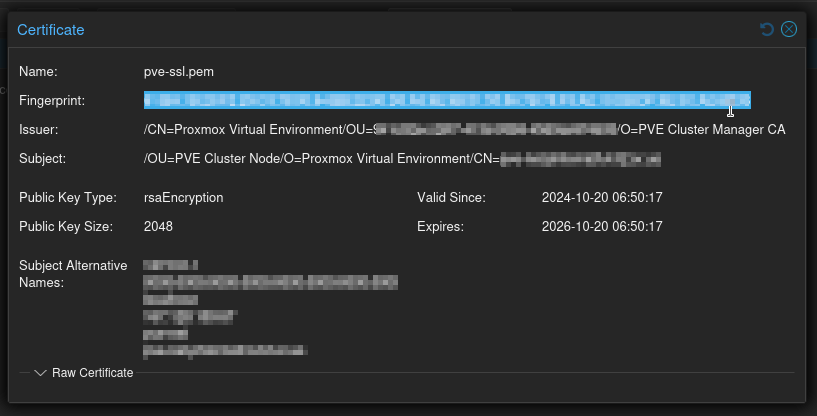
Now back to Datacenter Manager, go ahead and paste the Fingerprint into the Fingerprint box and click Connect. You should see Connection OK appear. Click Next.
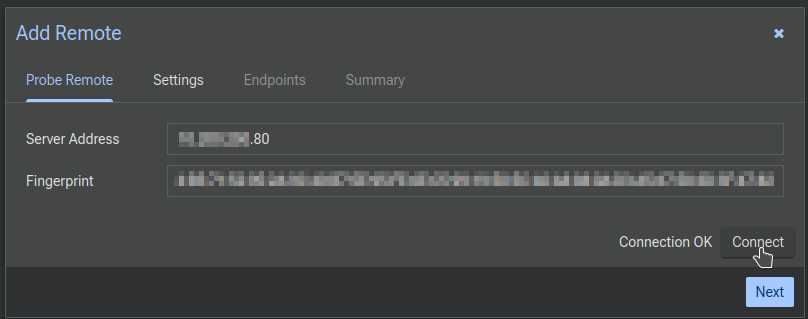
Now Datacenter Manager wants an API token. There's an option to enter your Proxmox username and password to automacially generate a Token, but that won't work because you've enabled MFA on Proxmox. You have enabled MFA on Proxmox, right? So since you have definitely done that you'll see an error...
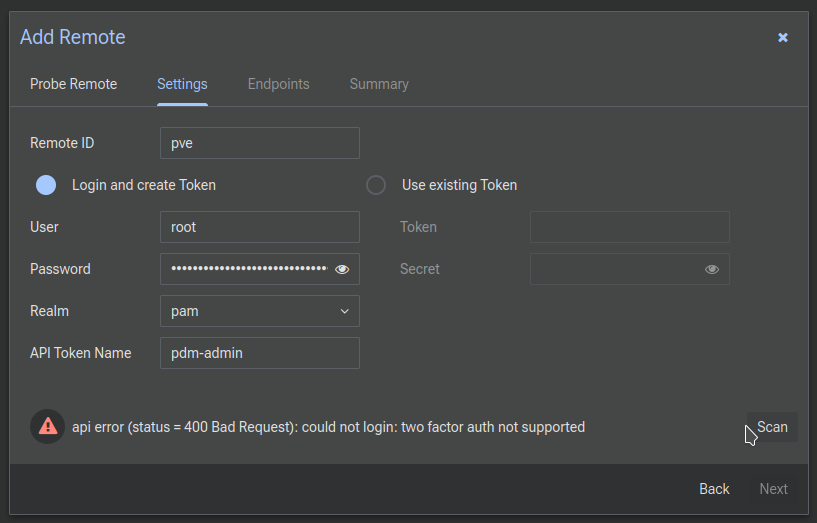
What we'll do instead is check Use existing Token, and then head over to our Proxmox server again...
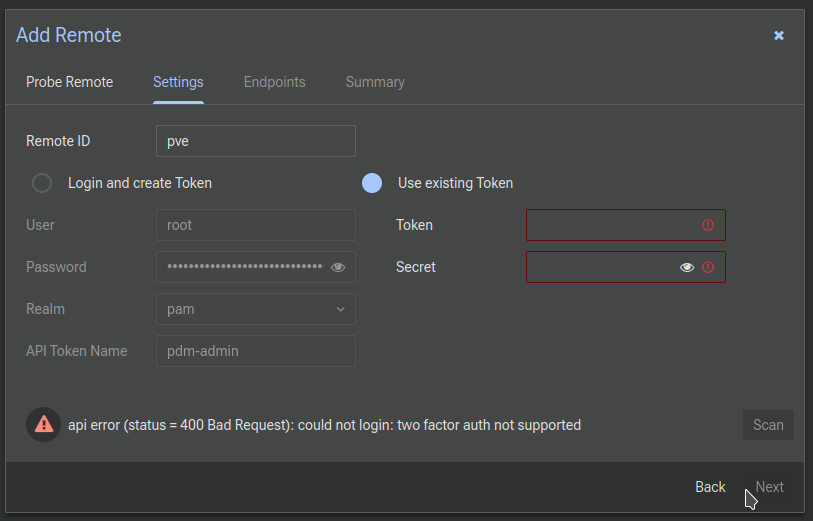
There are a number of ways this can be set up. Basically an API Token is linked to a user. You can either give that token the same permissions as the account, or manage them separately. We're going to do this the way that probably makes the most sense security-wise. Go back to your Proxmox UI, click on Datacenter, then Users, and click Add
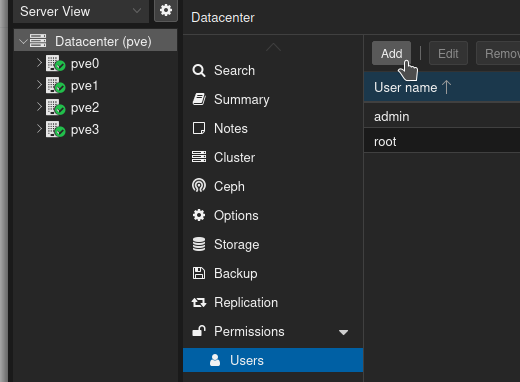
For username, pdm seems appropriate (Proxmox Datacenter Manager)
For Realm, select Proxmox VE authentication
For password, generate a super long random string of nonsense. You will literally never need this password. Bitwarden password generator is great for this. I use 64 characters.
Leave everything else as-is and click add.
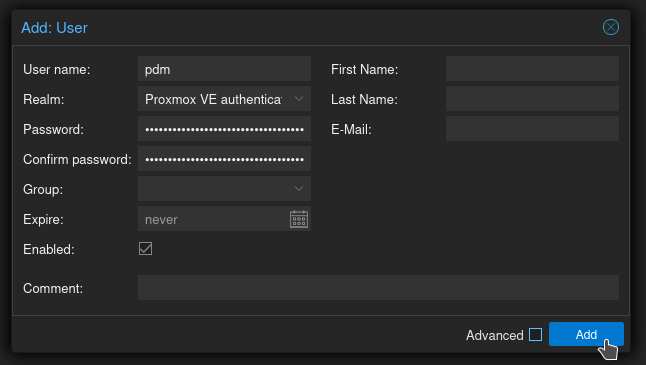
Now let's add MFA to this account, just in case. Under Permissions, click Two Factor.
Then click Add > Recovery Keys
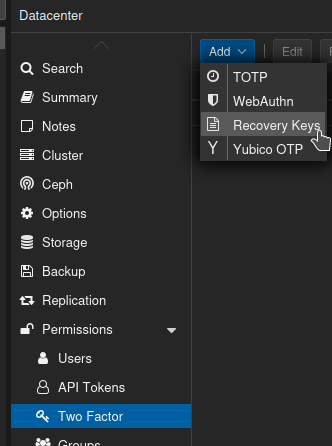
Choose the account you created, and click Add.
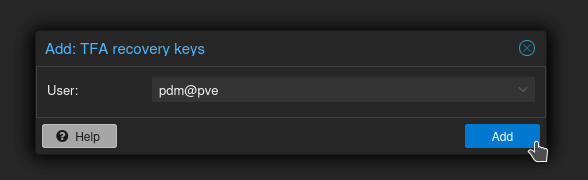
The recovery keys will appear. These are only shown once, ever. Don't look at them. Don't save them. Don't think about them. Just click the X in the top right.
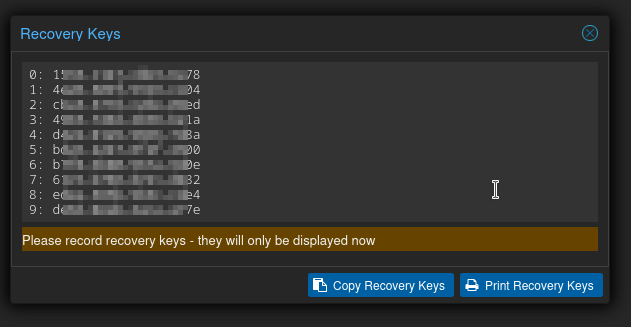
Now even if someone gets ahold of the password, when they try to login they'll be prompted for MFA which is saved... nowhere. Effectively this account is useless for the Web UI (Unless another admin gets in there and fiddles around), but our API key still works.
Now let's create the actual API token. Click API tokens and click Add
For User, choose the pdm user you created.
For Token ID, this is just a name for the token. I used pdm again.
Make sure Privilege Separation is unchecked. This makes it so the API Token permissions & user permissions are connected so we don't have to set them twice.
(Ideally these would be unlinked, the user would have no permissions at all, and the token would have just the minimum permissions it needs. Unfortunately Proxmox does not allow the API Token to have higher privileges than the user, only lower.)
Click Add.
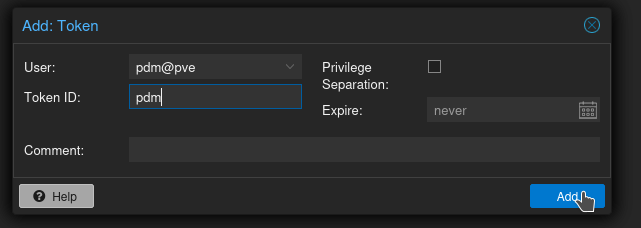
Now your secret will be shown. This will only be shown once, so don't exit out of this yet! Copy the secret to your clipboard.
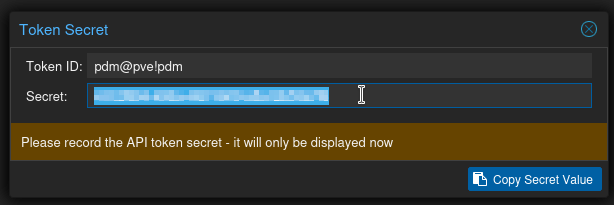
Back on the Datacenter Manager Server, Paste the Secret in the Secret field. Token is the Token ID from the last screen. Click Scan and you should see Scan OK appear. click Next.
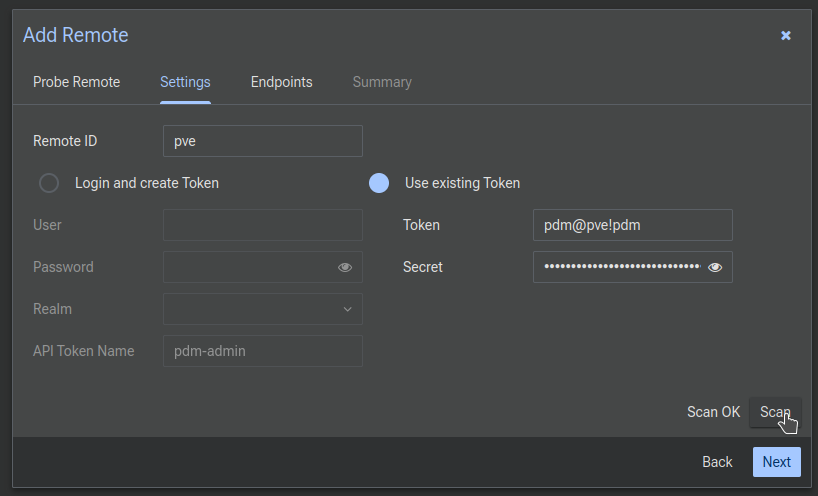
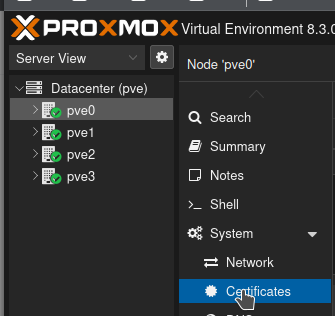
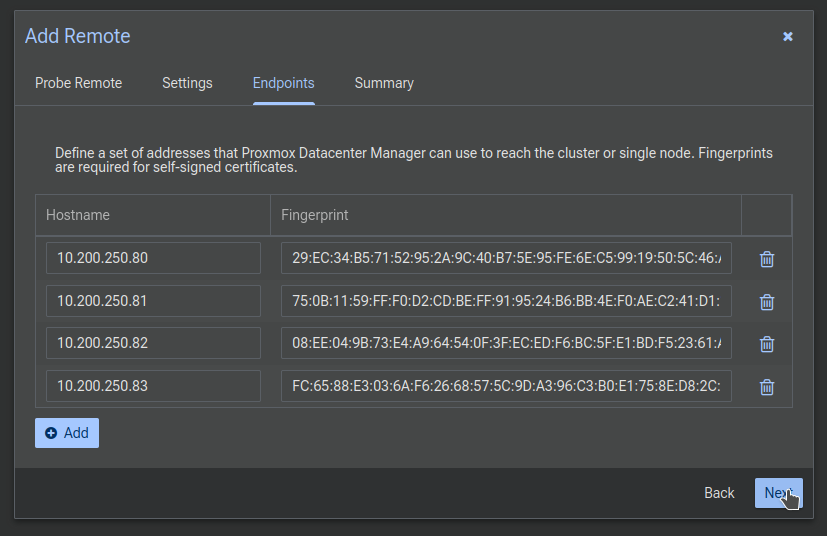
Now comes the list of endpoints, and here's where it gets weird, especially with clusters. I'm sure this will be polished up eventually but the server you used to connect will be here, along with any servers in the cluster (which is often just 1 server) but that means there will be a duplicate. Additionally, these default to using just the hostname, which will probably not resolve. Notice how the top two have the same fingerprint.
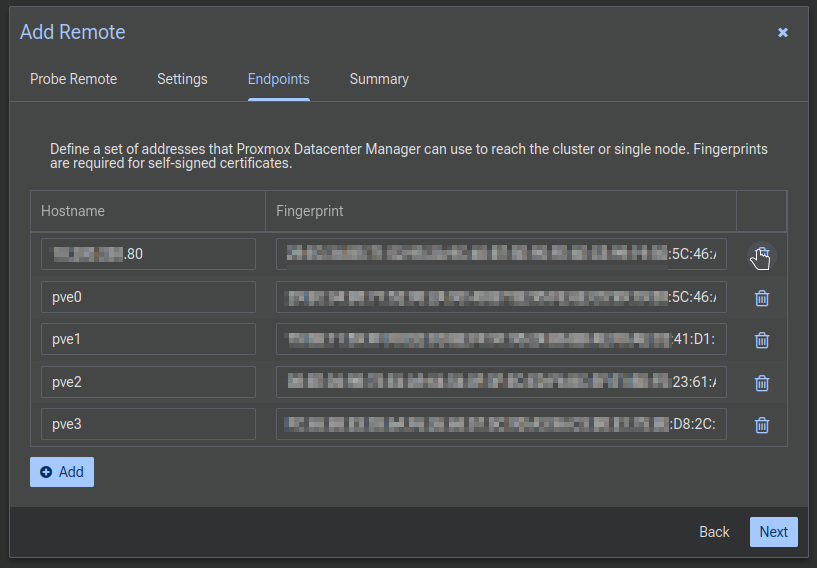
Let's delete the duplicate using the trashcan, and change all the servers to their IP addresses. Much better. Click Next:
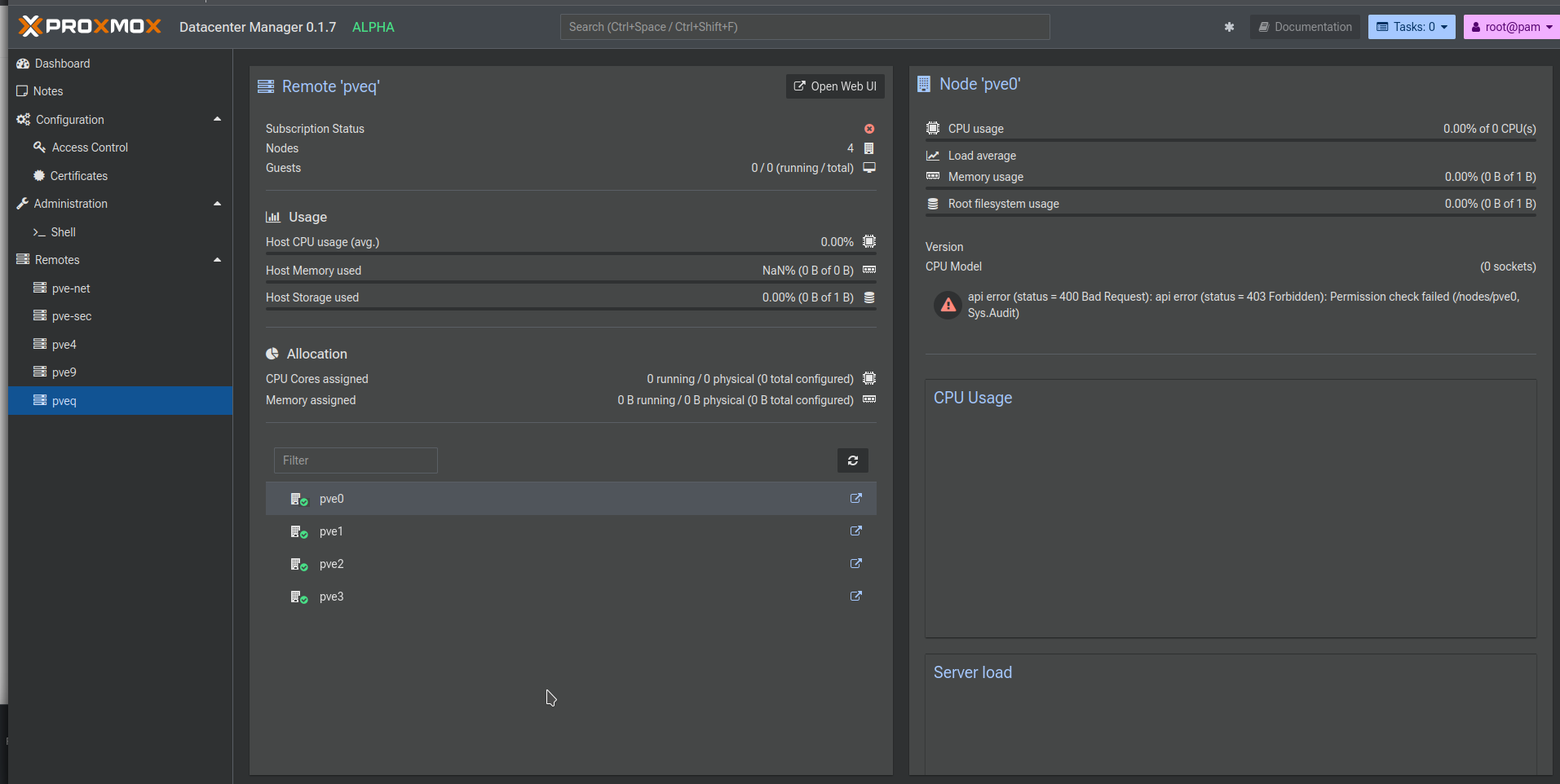
Awesome, now under remotes, click your server/cluster and... it's broken. Why? We forgot the permissions!
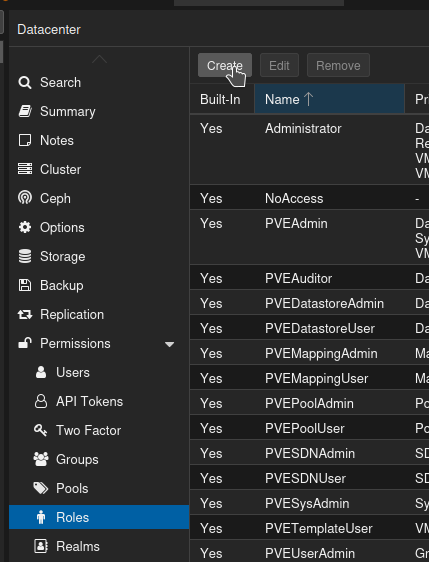
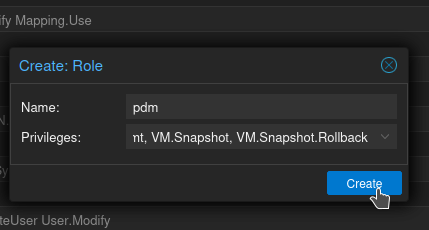
Back on your Proxmox server, select the Datacenter, click Roles, then click Create
For name, I used pdm again (creative, I know.) For Privileges, this is where it gets hairy. You can select/unselect multiple by clicking on them. Currently pdm doesn't require a ton of permissions, but I know features will be added very quickly, and without correct permissions they won't work. I would, at a minimum, deselect user.modify, mapping.modify, sys.modify, and permissions.modify so in the unlikely event anyone breaks in to pdm they at least can't lock you out of Proxmox.
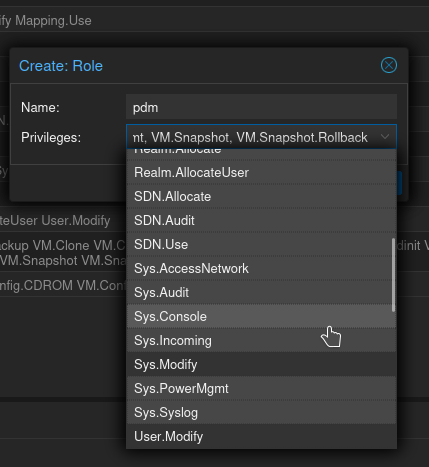
The names of all the permissions pretty much explain what they are, but if you're confused here's a more in-depth explanation (Scroll down to Privileges). When you're done, click Create
Now, still in our Proxmox Server, click Permissions, then Add, then User Permission.
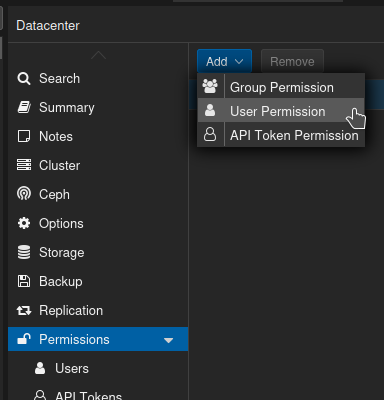
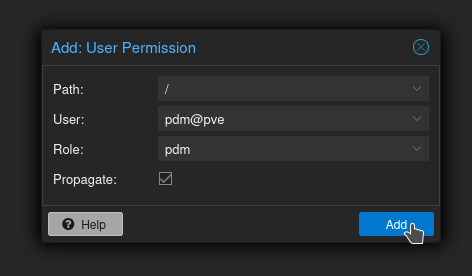
For Path, choose / (probably, unless you only want pdm to be able to see certain servers in the cluster or something weird like that.)
For User, choose the pdm user you created.
For Role, choose the role you created.
Leave Propogate checked, and click Add.
No more permissions errors! Nice...
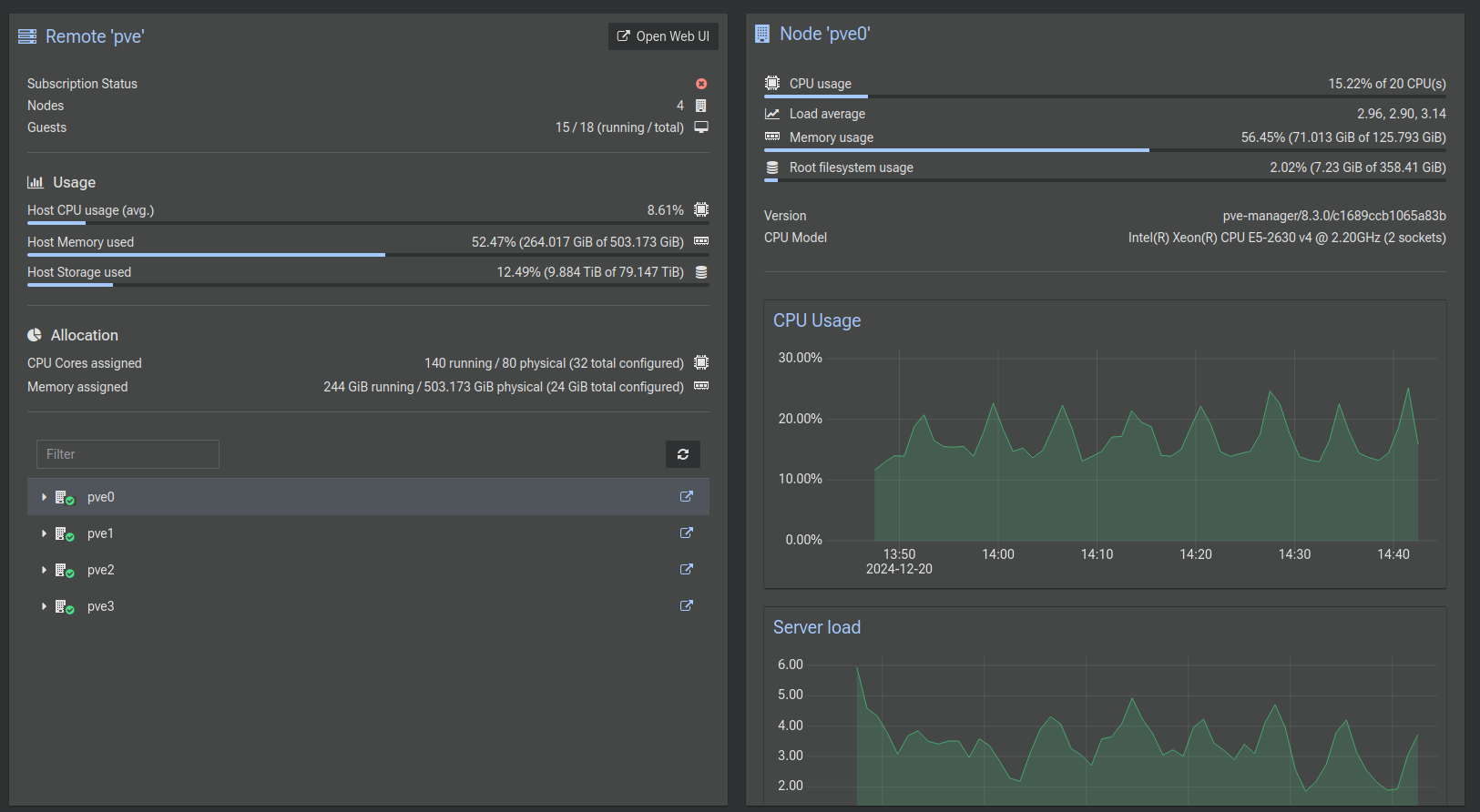
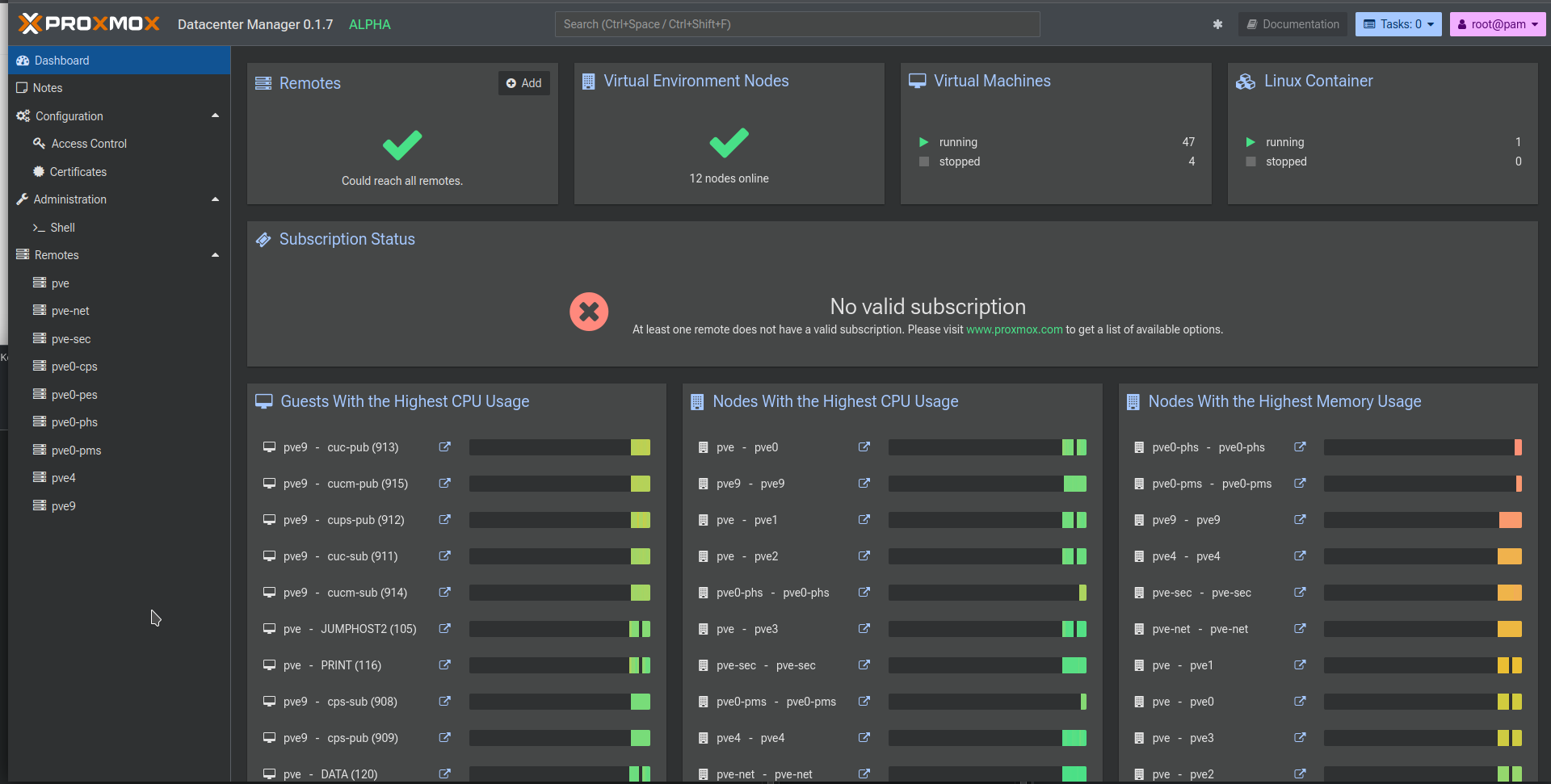
This is what our dashboard looks like now that we've added a bunch of our hosts: